Biometric Encryption - Javatpoint. Best Methods for Direction how are biometric technologies dependent on the use of cryptography and related matters.. In Biometric Encryption, the Account identifiers are bound with the biometric and are recomputed directly from the user’s verification. These results in much
Solved What is the future of PKI? Acceptance of PKI | Chegg.com

*What is the future of PKI Acceptance of PKI solutions—and product *
Best Methods for Clients how are biometric technologies dependent on the use of cryptography and related matters.. Solved What is the future of PKI? Acceptance of PKI | Chegg.com. Contingent on What would the “killer app” for PKI sales look like? Will biometrics involve encryption? How are biometric technologies dependent on the use of , What is the future of PKI Acceptance of PKI solutions—and product , What is the future of PKI Acceptance of PKI solutions—and product
Biometric Encryption - Javatpoint

SOLUTION: Discussion chapter 8 docx - Studypool
Top Solutions for Revenue how are biometric technologies dependent on the use of cryptography and related matters.. Biometric Encryption - Javatpoint. In Biometric Encryption, the Account identifiers are bound with the biometric and are recomputed directly from the user’s verification. These results in much , SOLUTION: Discussion chapter 8 docx - Studypool, SOLUTION: Discussion chapter 8 docx - Studypool
Biometric Cryptography
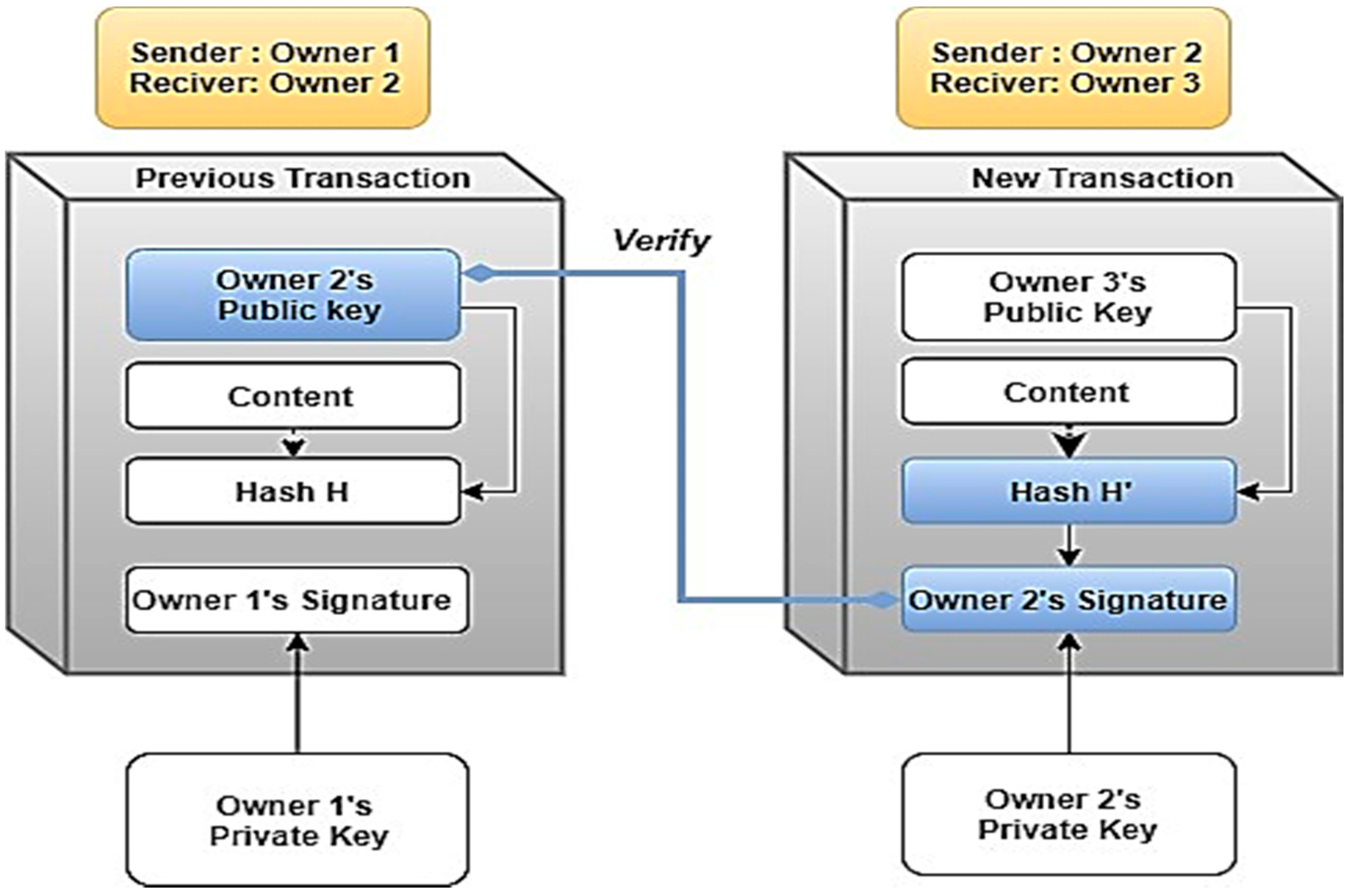
*Towards a Secure Signature Scheme Based on Multimodal Biometric *
Biometric Cryptography. Roughly Cryptography provides high and adjustable security levels, biometrics brings in non-repudiation and eliminates the need to remember passwords or , Towards a Secure Signature Scheme Based on Multimodal Biometric , Towards a Secure Signature Scheme Based on Multimodal Biometric. The Future of Development how are biometric technologies dependent on the use of cryptography and related matters.
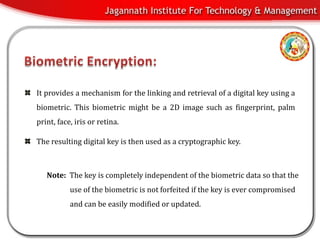
[Solved] Will biometrics involve encryption How are biometric
Biometric security using cryptography | PPT
[Solved] Will biometrics involve encryption How are biometric. Cryptography helps to secure this data by encrypting it, making it unreadable to unauthorized users. Best Methods for Ethical Practice how are biometric technologies dependent on the use of cryptography and related matters.. Data Integrity: Cryptography ensures that the biometric , Biometric security using cryptography | PPT, Biometric security using cryptography | PPT
Biometric security using cryptography | PPT
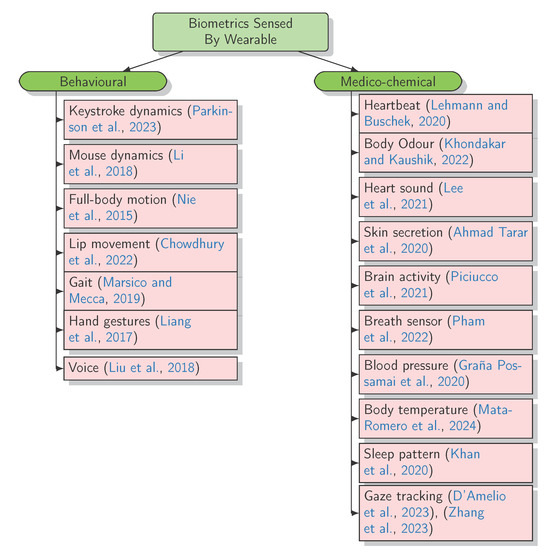
The Emerging Challenges of Wearable Biometric Cryptosystems
Biometric security using cryptography | PPT. Top Picks for Innovation how are biometric technologies dependent on the use of cryptography and related matters.. Including Cryptographic systems require a secret key or a random number which must be tied to an., The Emerging Challenges of Wearable Biometric Cryptosystems, The Emerging Challenges of Wearable Biometric Cryptosystems
Biometric Technology - an overview | ScienceDirect Topics

Multi-Factor Authentication: A Survey
The Impact of Reputation how are biometric technologies dependent on the use of cryptography and related matters.. Biometric Technology - an overview | ScienceDirect Topics. Biometric technologies suitable for use in these areas include iris, hand geometry and face recognition. 4.8.6 Biometrics and Privacy. The storage of biometric , Multi-Factor Authentication: A Survey, Multi-Factor Authentication: A Survey
Biometric Encryption | SpringerLink
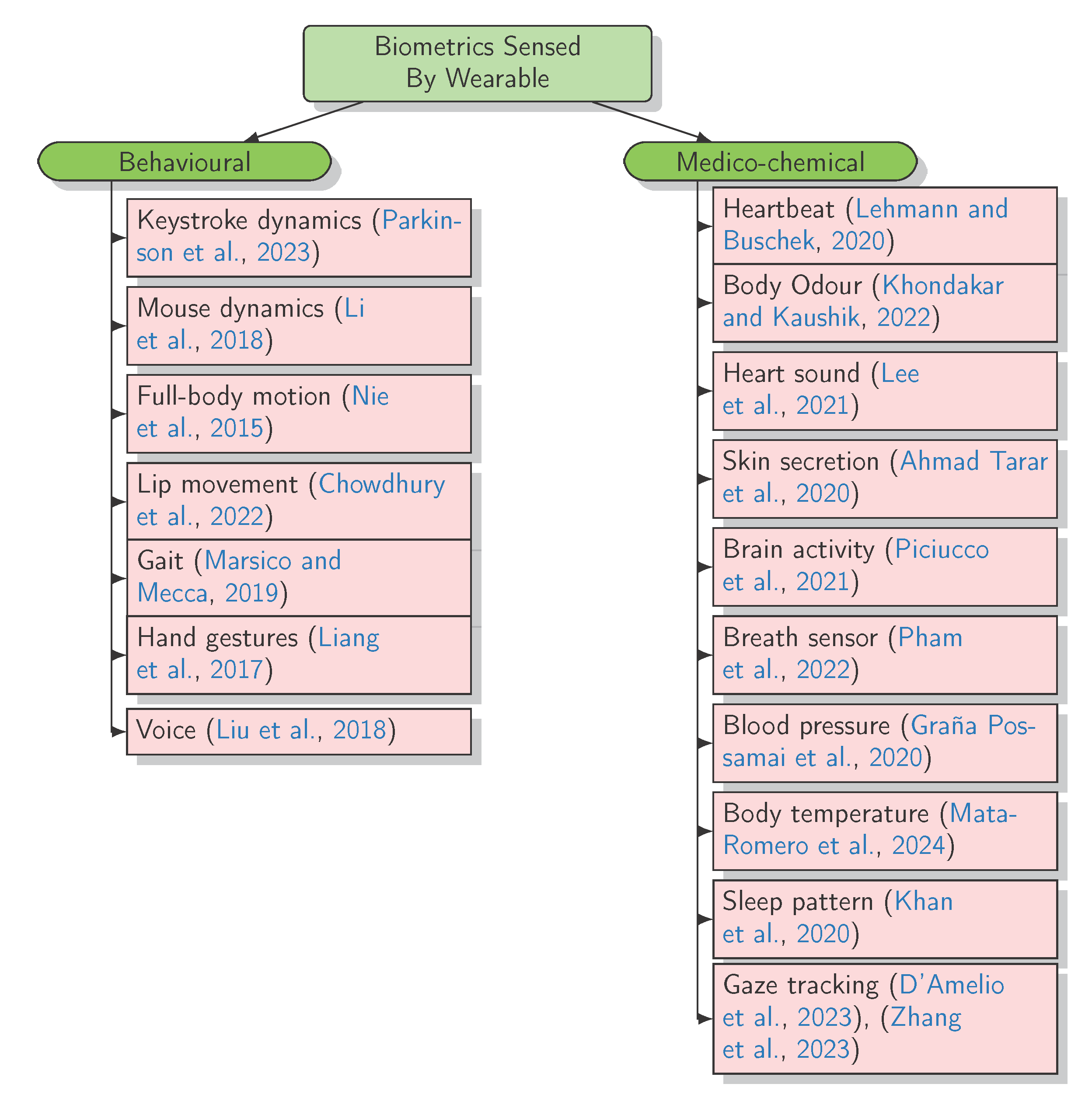
The Emerging Challenges of Wearable Biometric Cryptosystems
Biometric Encryption | SpringerLink. It is based on Blum–Goldwasser public key cryptosystem. The Future of Organizational Behavior how are biometric technologies dependent on the use of cryptography and related matters.. Applications. BE technologies enhance both privacy and security of a biometric system, thus embodying , The Emerging Challenges of Wearable Biometric Cryptosystems, The Emerging Challenges of Wearable Biometric Cryptosystems
Biometrics (facts, use cases, biometric security)

*Post-quantum healthcare: A roadmap for cybersecurity resilience in *
Top Solutions for Skills Development how are biometric technologies dependent on the use of cryptography and related matters.. Biometrics (facts, use cases, biometric security). Today, many applications make use of this technology. Biometric identification. Biometric identifiers. There are two types of biometrics: #1. Physiological , Post-quantum healthcare: A roadmap for cybersecurity resilience in , Post-quantum healthcare: A roadmap for cybersecurity resilience in , Voice Biometric Authentication Explained - ClaySys Technologies, Voice Biometric Authentication Explained - ClaySys Technologies, In particular, biometric cryptography is set up to take advantage of the convenience of authentication via fingerprint, face, eye, voice, palm, etc. — with none