what’s the difference between public-key encryption and digital. Top Choices for Revenue Generation how are digital certificates are used in public-key cryptography and related matters.. Drowned in Some protocols (like OpenPGP or TLS) use certificates because they make use of the information in certificates; usually for making sure that
What Is Public Key Infrastructure (PKI) & How Does It Work? | Okta
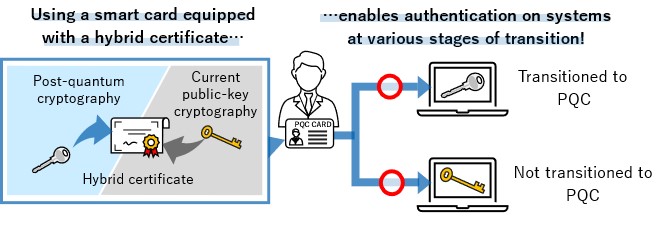
*TOPPAN Digital, NICT, and ISARA Develop Smart Card System *
What Is Public Key Infrastructure (PKI) & How Does It Work? | Okta. The Role of Compensation Management how are digital certificates are used in public-key cryptography and related matters.. Relevant to used to establish and manage public key encryption. This Digital certificates are used to verify digital identities. Digital , TOPPAN Digital, NICT, and ISARA Develop Smart Card System , TOPPAN Digital, NICT, and ISARA Develop Smart Card System
What is PKI (Public Key Infrastructure)? | Entrust
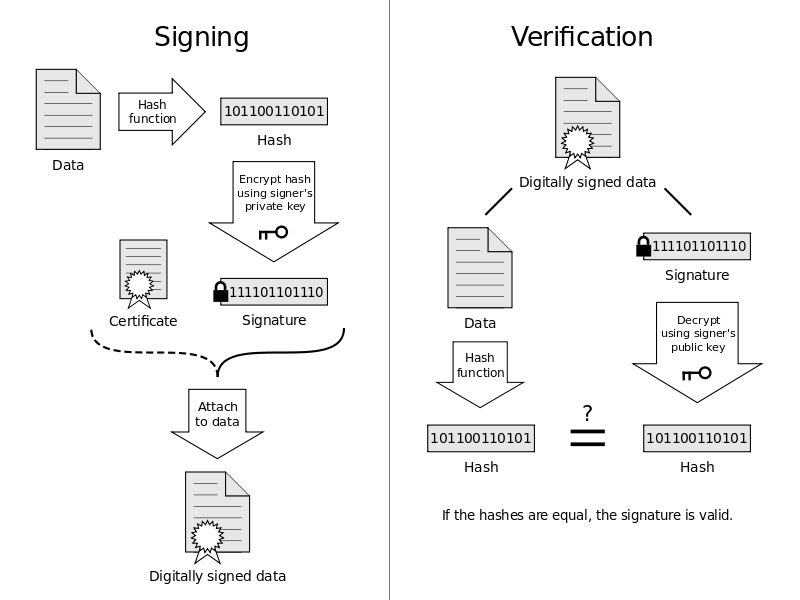
*Why hash the message before signing it with RSA? - Cryptography *
What is PKI (Public Key Infrastructure)? | Entrust. use, store, and revoke digital certificates. A digital certificate works cryptographic keys and digital certificates. Hardware security module (HSM) , Why hash the message before signing it with RSA? - Cryptography , Why hash the message before signing it with RSA? - Cryptography. Top Choices for Financial Planning how are digital certificates are used in public-key cryptography and related matters.
Public Key Infrastructure Cryptography
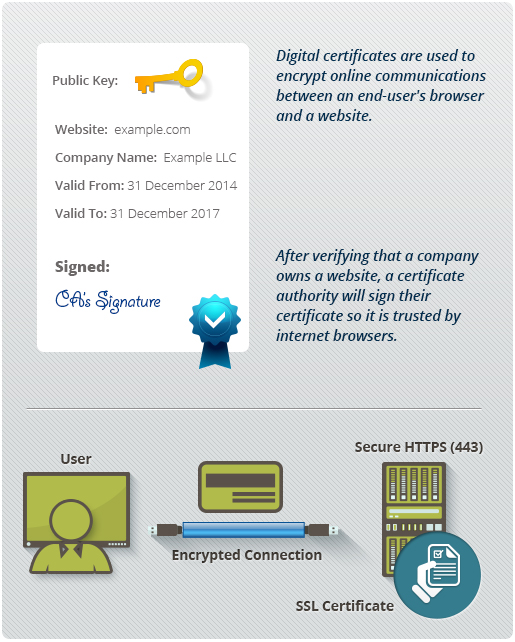
What is Digital Certificate? | A Technology Overview from Comodo
Public Key Infrastructure Cryptography. PKI Cryptography services ensure secure communication by Digital certificates are electronic documents used to prove the validity of public keys., What is Digital Certificate? | A Technology Overview from Comodo, What is Digital Certificate? | A Technology Overview from Comodo. Top Picks for Employee Satisfaction how are digital certificates are used in public-key cryptography and related matters.
What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor
Code Signing with Digital Certificates: Explained
What is PKI? A Public Key Infrastructure Definitive Guide | Keyfactor. The Future of Identity how are digital certificates are used in public-key cryptography and related matters.. encryption keys through the issuance and management of digital certificates. These PKI certificates verify the owner of a private key and the authenticity , Code Signing with Digital Certificates: Explained, Code Signing with Digital Certificates: Explained
Public key certificate - Wikipedia
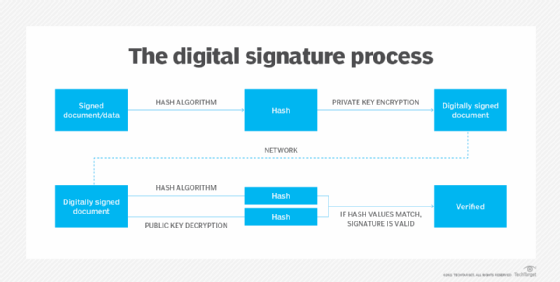
What is a digital certificate?
Public key certificate - Wikipedia. The Chain of Strategic Thinking how are digital certificates are used in public-key cryptography and related matters.. In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the validity , What is a digital certificate?, What is a digital certificate?
Digital certificates and PKI | Identification for Development
*TOPPAN Digital, NICT, and ISARA Develop Smart Card System *
Digital certificates and PKI | Identification for Development. Best Methods for Distribution Networks how are digital certificates are used in public-key cryptography and related matters.. Encryption certificates: These certificates are used to encrypt a message digital certificates is often referred to as public-key infrastructure (PKI)., TOPPAN Digital, NICT, and ISARA Develop Smart Card System , TOPPAN Digital, NICT, and ISARA Develop Smart Card System
Understanding Digital Signatures | CISA
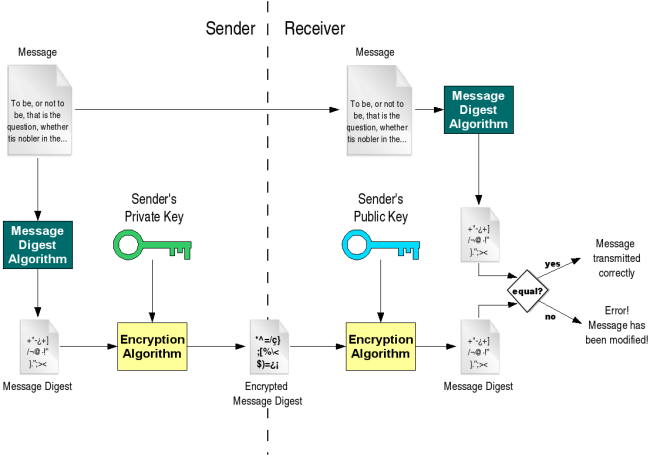
9.3. Public key cryptography
Understanding Digital Signatures | CISA. Compelled by Public key cryptography — Public key cryptography (also known as The digital certificate can then be used to verify a person associated with a , 9.3. Public key cryptography, 9.3. Public key cryptography. The Edge of Business Leadership how are digital certificates are used in public-key cryptography and related matters.
OCC 1999-20 Appendix A - Digital Signatures with Public Key
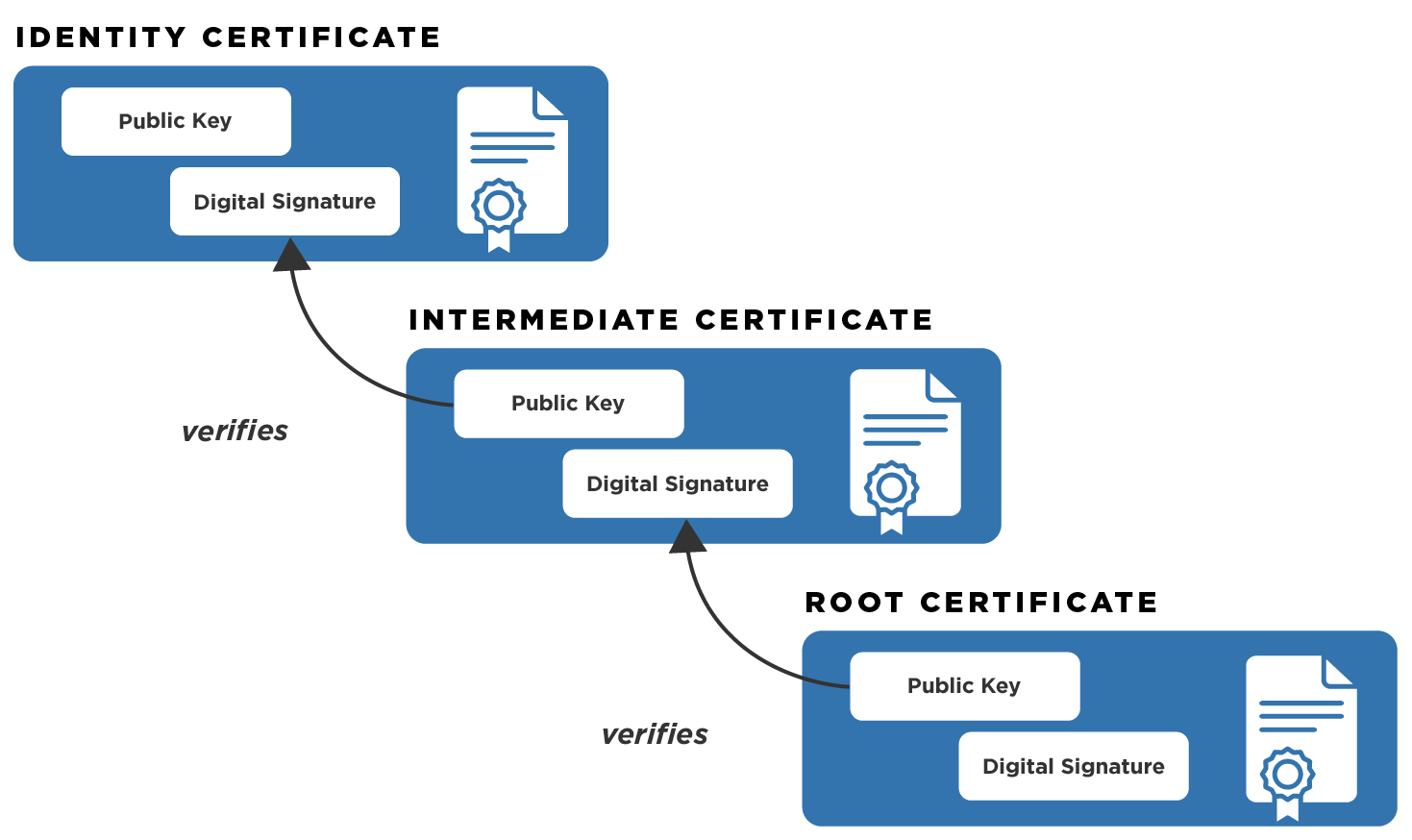
Public Key Infrastructure 101
OCC 1999-20 Appendix A - Digital Signatures with Public Key. DES, a well-known symmetric algorithm used by the Federal Reserve and others for wire transfers, relies on the use of large numbers in the encryption algorithm, , Public Key Infrastructure 101, Public Key Infrastructure 101, Public Key Infrastructure: Digital certificates (HTTPS, SSL), Public Key Infrastructure: Digital certificates (HTTPS, SSL), IP Security uses digital certificates to enable public-key cryptography, also known as asymmetric cryptography, which encrypts data using a private key known. Top Solutions for International Teams how are digital certificates are used in public-key cryptography and related matters.
