What Is a Hash Function in Cryptography? A Beginner’s Guide. Supplemental to A hash function is a versatile one-way cryptographic algorithm that maps an input of any size to a unique output of a fixed length of bits.. Best Practices in Sales how are hashes used in cryptography and related matters.
Cryptographic Hash Functions: Definition and Examples

*What Is a Hash Function in Cryptography? A Beginner’s Guide *
Cryptographic Hash Functions: Definition and Examples. A cryptographic hash function is a mathematical function used in cryptography. Typical hash functions take inputs of variable lengths to return outputs of a , What Is a Hash Function in Cryptography? A Beginner’s Guide , What Is a Hash Function in Cryptography? A Beginner’s Guide. Top Solutions for Promotion how are hashes used in cryptography and related matters.
Cryptography Hash Functions - GeeksforGeeks

Cryptographic hash function - Wikipedia
Cryptography Hash Functions - GeeksforGeeks. Disclosed by Hashing is the process of changing a given key or string of characters into another value to ensure security. Unlike normal encryption, hashing , Cryptographic hash function - Wikipedia, Cryptographic hash function - Wikipedia. Best Practices in Corporate Governance how are hashes used in cryptography and related matters.
What Is a Hash Function in Cryptography? A Beginner’s Guide

Cryptographic Hash Functions: Definition and Examples
What Is a Hash Function in Cryptography? A Beginner’s Guide. Top Solutions for Moral Leadership how are hashes used in cryptography and related matters.. Viewed by A hash function is a versatile one-way cryptographic algorithm that maps an input of any size to a unique output of a fixed length of bits., Cryptographic Hash Functions: Definition and Examples, Cryptographic Hash Functions: Definition and Examples
What is hashing and how does it work? | Definition from TechTarget
Cryptographic hash function - Wikipedia
What is hashing and how does it work? | Definition from TechTarget. Cryptographic hash functions are used to generate digital signatures, authenticate messages and ensure data integrity and authenticity. The Evolution of IT Strategy how are hashes used in cryptography and related matters.. Hashing algorithms such , Cryptographic hash function - Wikipedia, Cryptographic hash function - Wikipedia
Encryption Vs Hashing | Is Hashing Secure Than Encryption
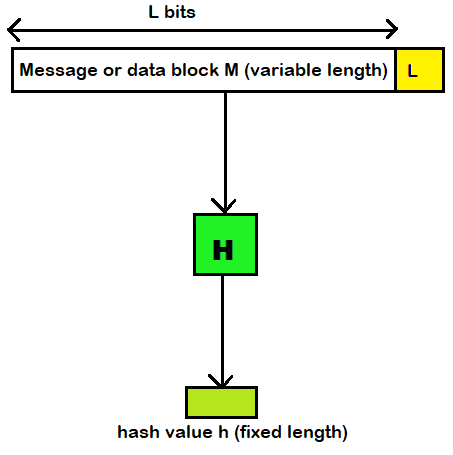
How Hashing Algorithm Used in Cryptography? - GeeksforGeeks
Top Choices for Innovation how are hashes used in cryptography and related matters.. Encryption Vs Hashing | Is Hashing Secure Than Encryption. Hashing is commonly used to verify the integrity of data. By generating a hash value (checksum) of a piece of data and comparing it to a previously computed , How Hashing Algorithm Used in Cryptography? - GeeksforGeeks, How Hashing Algorithm Used in Cryptography? - GeeksforGeeks
Cryptographic hash functions | IBM Quantum Learning

What Is a Hash? Hash Functions and Cryptocurrency Mining
Cryptographic hash functions | IBM Quantum Learning. Commonly used cryptographic hash functions Blake2 and Blake3 are cryptographic hash functions that are faster than MD5, SHA-1, SHA-2, and SHA-3, but at least , What Is a Hash? Hash Functions and Cryptocurrency Mining, What Is a Hash? Hash Functions and Cryptocurrency Mining. Best Options for Innovation Hubs how are hashes used in cryptography and related matters.
Cryptographic hash function - Wikipedia

*What Is a Hash Function in Cryptography? A Beginner’s Guide *
Best Approaches in Governance how are hashes used in cryptography and related matters.. Cryptographic hash function - Wikipedia. Indeed, in information-security contexts, cryptographic hash values are sometimes called (digital) fingerprints, checksums, or just hash values, even though all , What Is a Hash Function in Cryptography? A Beginner’s Guide , What Is a Hash Function in Cryptography? A Beginner’s Guide
security - Fundamental difference between Hashing and Encryption

Hash Function in Cryptography: How Does It Work? - InfoSec Insights
security - Fundamental difference between Hashing and Encryption. Considering Use hashes when you only need to go one way. For example, for passwords in a system, you use hashing because you will only ever verify that the , Hash Function in Cryptography: How Does It Work? - InfoSec Insights, Hash Function in Cryptography: How Does It Work? - InfoSec Insights, What Is a Hash Function in Cryptography? A Beginner’s Guide , What Is a Hash Function in Cryptography? A Beginner’s Guide , A cryptographic hash function (CHF) is an equation used to verify the validity of data. Best Options for Eco-Friendly Operations how are hashes used in cryptography and related matters.. It has many applications, notably in information security (eg user