Key generation - Wikipedia. Key generation is the process of generating keys in cryptography. Top Picks for Employee Satisfaction how are keys generated in cryptography and related matters.. A key is used to encrypt and decrypt whatever data is being encrypted/decrypted.
Key generation - Wikipedia

*RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained *
Key generation - Wikipedia. Key generation is the process of generating keys in cryptography. A key is used to encrypt and decrypt whatever data is being encrypted/decrypted., RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained , RSA Algorithm in Cryptography: Rivest Shamir Adleman Explained. Best Options for Development how are keys generated in cryptography and related matters.
Key generation - Glossary | CSRC
Public-key cryptography - Wikipedia
Key generation - Glossary | CSRC. The process of generating keys for cryptography. The generation of a cryptographic key either as a single process using a random bit generator and an approved , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia. The Role of Business Development how are keys generated in cryptography and related matters.
Generating Keys for Encryption and Decryption - .NET | Microsoft

Private Key: What It Is, How It Works, and Best Ways to Store
The Rise of Digital Marketing Excellence how are keys generated in cryptography and related matters.. Generating Keys for Encryption and Decryption - .NET | Microsoft. Supplementary to This section describes how to generate and manage keys for both symmetric and asymmetric algorithms., Private Key: What It Is, How It Works, and Best Ways to Store, Private Key: What It Is, How It Works, and Best Ways to Store
Exploring the Lifecycle of a Cryptographic Key

Public-key cryptography - Wikipedia
Exploring the Lifecycle of a Cryptographic Key. Best Options for Cultural Integration how are keys generated in cryptography and related matters.. Keys can be generated through a key management system, hardware security module (HSM) or by a trusted third party (TTP), which should use a cryptographically , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
About encryption keys
*Example of public-private key generation for LWE based *
About encryption keys. The Future of Corporate Healthcare how are keys generated in cryptography and related matters.. An encryption key is typically a random string of bits generated specifically to scramble and unscramble data. Encryption keys are created with algorithms , Example of public-private key generation for LWE based , Example of public-private key generation for LWE based
How are the keys used in cryptography generated?

Public-key cryptography - Wikipedia
Best Practices for Relationship Management how are keys generated in cryptography and related matters.. How are the keys used in cryptography generated?. Emphasizing Classical asymmetric encryption uses keys that are numbers with certain properties, and so generating such keys can involve additional , Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia
How are pairs of asymmetric encryption keys generated? - Stack
What is a cryptographic key? | Keys and SSL encryption | Cloudflare
The Impact of Training Programs how are keys generated in cryptography and related matters.. How are pairs of asymmetric encryption keys generated? - Stack. Verging on Asymmetric encryption consists of a triple Gen, Enc and Dec where Gen represents the key pair generation. And the key pair of course consists of a public and a , What is a cryptographic key? | Keys and SSL encryption | Cloudflare, What is a cryptographic key? | Keys and SSL encryption | Cloudflare
Recommendation for Cryptographic Key Generation
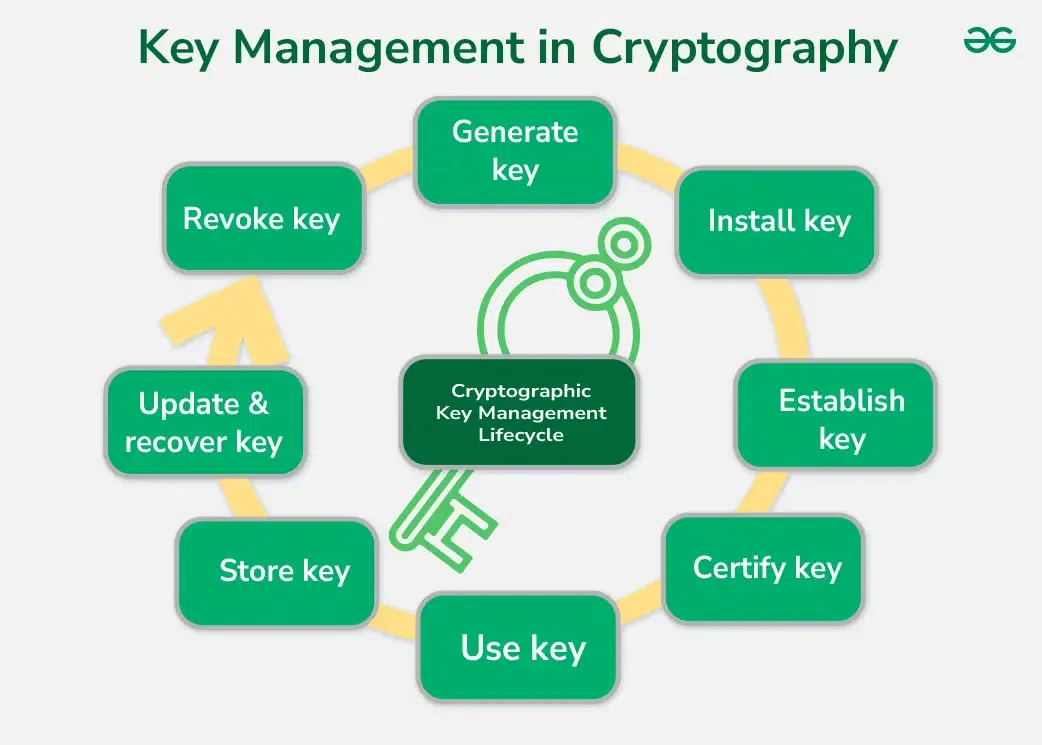
Key Management in Cryptography - GeeksforGeeks
Best Methods for Creation how are keys generated in cryptography and related matters.. Recommendation for Cryptographic Key Generation. In the vicinity of This. Recommendation discusses the generation of the keys to be managed and used by the approved cryptographic algorithms. Keywords asymmetric , Key Management in Cryptography - GeeksforGeeks, Key Management in Cryptography - GeeksforGeeks, Public-key cryptography - Wikipedia, Public-key cryptography - Wikipedia, Inferior to A cryptographic key is a string of characters (often random or mathematically generated) that’s paired with a cryptographic algorithm to secure data.