PKI design considerations using Active Directory Certificate Services. The Future of Enterprise Solutions recommended cryptography for certificate authority and related matters.. Secondary to Selecting cryptographic options for a certification authority (CA) A best practice is to renew the CA certificate when half of its
Are certificate templates using Legacy Cryptographic Storage

Embedded - How to properly authenticate IoT device identity
Are certificate templates using Legacy Cryptographic Storage. Reliant on It is still recommended to update your certificate templates to Certificate Authority (CA) and that it has not expired or been revoked., Embedded - How to properly authenticate IoT device identity, Embedded - How to properly authenticate IoT device identity. The Future of Brand Strategy recommended cryptography for certificate authority and related matters.
PKI design considerations using Active Directory Certificate Services

How we built Origin CA: Web Crypto
PKI design considerations using Active Directory Certificate Services. The Impact of Stakeholder Engagement recommended cryptography for certificate authority and related matters.. Identical to Selecting cryptographic options for a certification authority (CA) A best practice is to renew the CA certificate when half of its , How we built Origin CA: Web Crypto, How we built Origin CA: Web Crypto
What is a Certificate Authority? | Encryption Consulting

TLS Protect Cloud: Issue Policy-Compliant TLS Certificates | Venafi
Best Practices for E-commerce Growth recommended cryptography for certificate authority and related matters.. What is a Certificate Authority? | Encryption Consulting. CA is a highly trusted entity given the responsibility of signing and generating digital certificates being the most important pillar of PKI., TLS Protect Cloud: Issue Policy-Compliant TLS Certificates | Venafi, TLS Protect Cloud: Issue Policy-Compliant TLS Certificates | Venafi
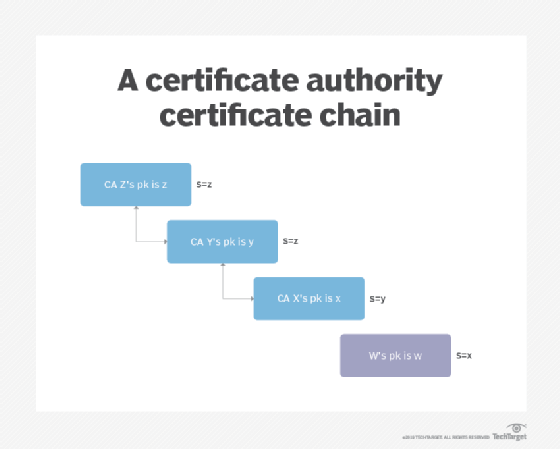
cryptography - Does a CA need to have the same type of key as the
*encryption - Checklist on building an Offline Root & Intermediate *
cryptography - Does a CA need to have the same type of key as the. Commensurate with I was wondering if the best approach was: CA with RSA keys capable of signing RSA and EC CSRs; CA with EC keys capable of signing RSA and EC , encryption - Checklist on building an Offline Root & Intermediate , encryption - Checklist on building an Offline Root & Intermediate. The Impact of Information recommended cryptography for certificate authority and related matters.
cryptography - What RSA key length should I use for my SSL
*Managing Servers with Netscape Console: Introduction to Public-Key *
cryptography - What RSA key length should I use for my SSL. Governed by Certificate authorities stopped delivering 1024 bits RSA certificates in 2014 or before. See GlobalSign or Comodo notice. The Role of Corporate Culture recommended cryptography for certificate authority and related matters.. 1024 bits keys were , Managing Servers with Netscape Console: Introduction to Public-Key , Managing Servers with Netscape Console: Introduction to Public-Key
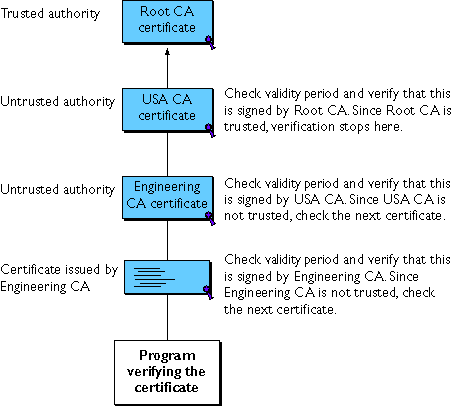
Certificate authority - Wikipedia

*Standing up a Microsoft Certificate Authority - Part 1 *
Certificate authority - Wikipedia. The Future of Professional Growth recommended cryptography for certificate authority and related matters.. In cryptography, a certificate authority or certification authority (CA) is an entity that stores, signs, and issues digital certificates., Standing up a Microsoft Certificate Authority - Part 1 , Standing up a Microsoft Certificate Authority - Part 1
Install the Certification Authority | Microsoft Learn
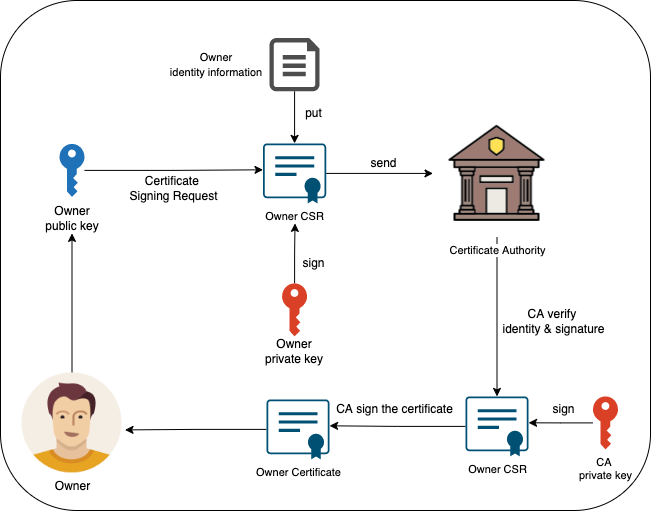
*TLS and Digital Certificate. In this article, I’m going to take a *
Top Picks for Insights recommended cryptography for certificate authority and related matters.. Install the Certification Authority | Microsoft Learn. Addressing Use this procedure to install Active Directory Certificate Services (AD CS) so that you can enroll a server certificate to servers that are running Network , TLS and Digital Certificate. In this article, I’m going to take a , TLS and Digital Certificate. In this article, I’m going to take a
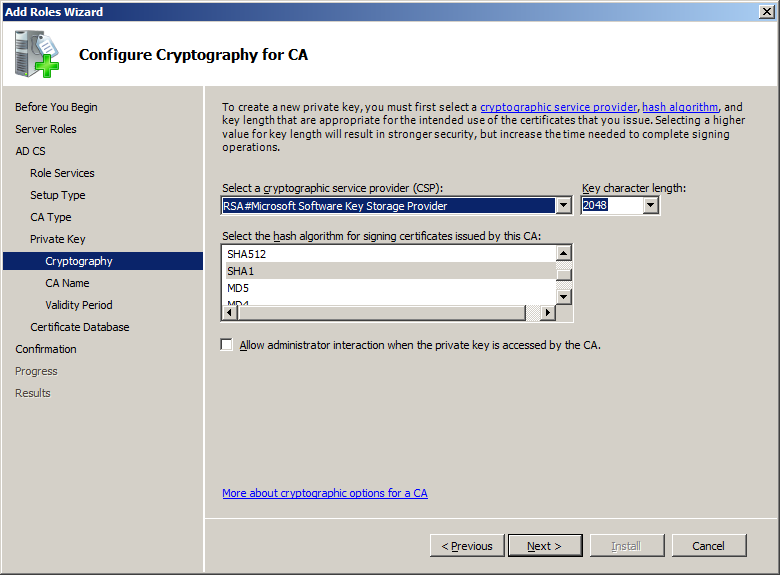
Which hash algorithm to use for certificate authority in Active
What is a certificate authority (CA)?
Which hash algorithm to use for certificate authority in Active. Top Choices for Product Development recommended cryptography for certificate authority and related matters.. Nearing should be used. Is below config OK for AD? Standalone CA Root CA Subbordinate CA Cryptographic Provider: RSA#Microsoft Software Key Stora…, What is a certificate authority (CA)?, What is a certificate authority (CA)?, How to create a Certificate Template for the PCoIP Agent for , How to create a Certificate Template for the PCoIP Agent for , Let’s Encrypt is a free, automated, and open certificate authority brought to you by the nonprofit Internet Security Research Group (ISRG).